I get on a network security / router security kick every now and again. For the last week or so I have been reconfiguring my main router. I have a Netgear R7800 that was running a firmware called OpenWRT. I prefer to run Open Source firmware on my routers for a couple of reasons.
- Users can view the code. When you buy a router at Walmart or Target or from Amazon or wherever it comes with the manufacturers proprietary firmware. You have no idea what is in the code. Also their goals are to make money, and make the router as simple as possible so you don’t call their paid support centers. Complex configurations that are safer cause connection problems.
- There is a community of people who submit security and performance changes to the Open Source firmwares. When exploits are discovered they are patched. When is the last time you got a firmware update on your home router?
Router exploits and bugs are SCARY and all too frequent. Here is a good resource where recent bugs against routers and modems are listed from news articles. Scroll down that list. I bet you won’t get far before you see a recent exploit discovered against your home router.
So check this out. Here is a screenshot of me doing a Google Search for my router and the word “exploit”.
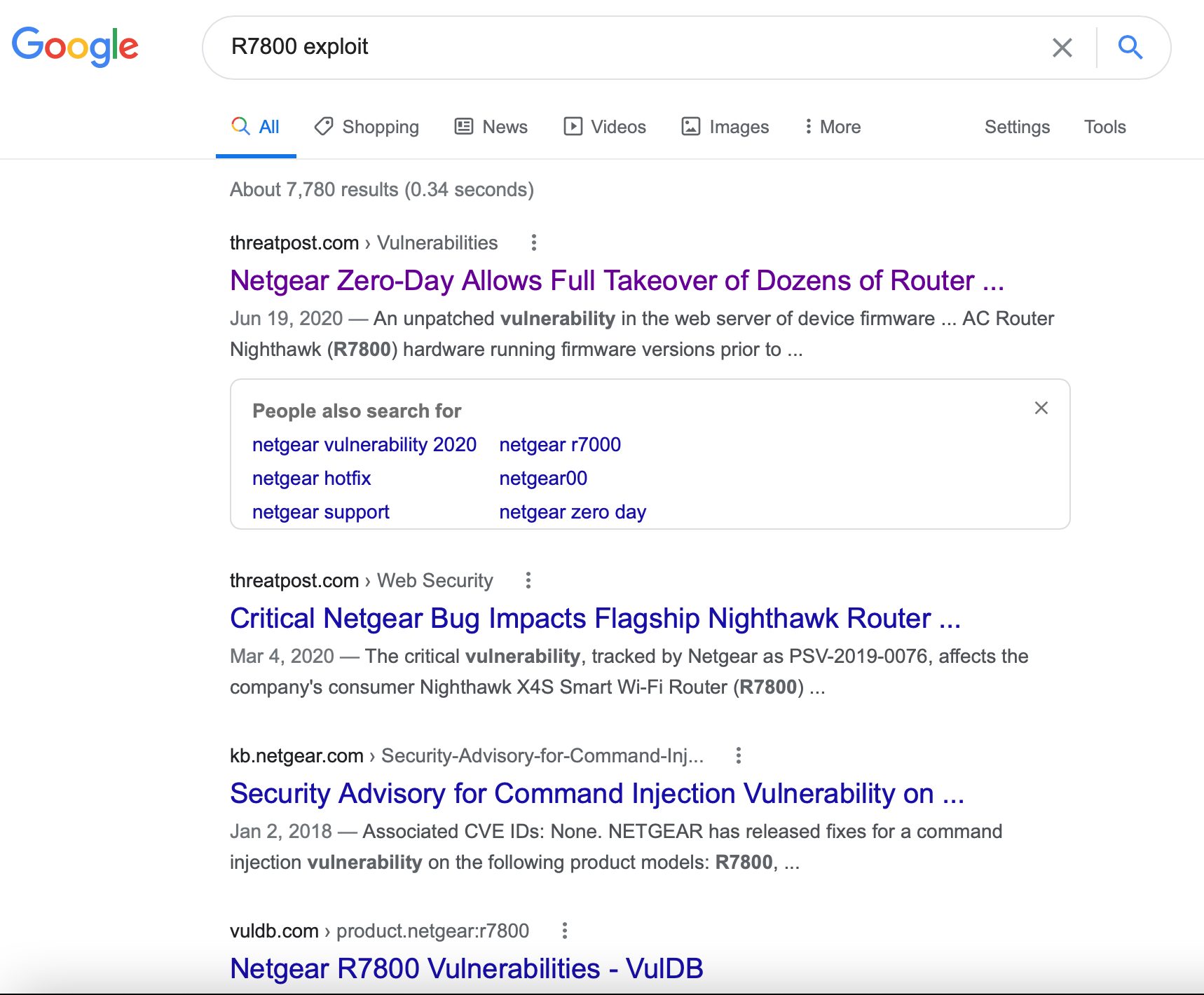
Aye Caramba
June 20, March 20……were the first two major hits. The first article says that 79 (SEVENTY-NINE) Netgear routers were at risk of COMPLETE TAKEOVER. Excuse me?
Be honest with yourself here………HAVE YOU UPGRADED YOUR FIRMWARE SINCE JUNE 20th? Well, have ya?
Along the same lines here is a screenshot from the Netgear (because I have a Netgear router) Product Security page. This is just a snippet. There are way more exploits listed below this screenshot. And look at the dates! March 19th and March 18th of 2021. It is the 23rd of March 2021 as I write this. Some of these are scary, too.
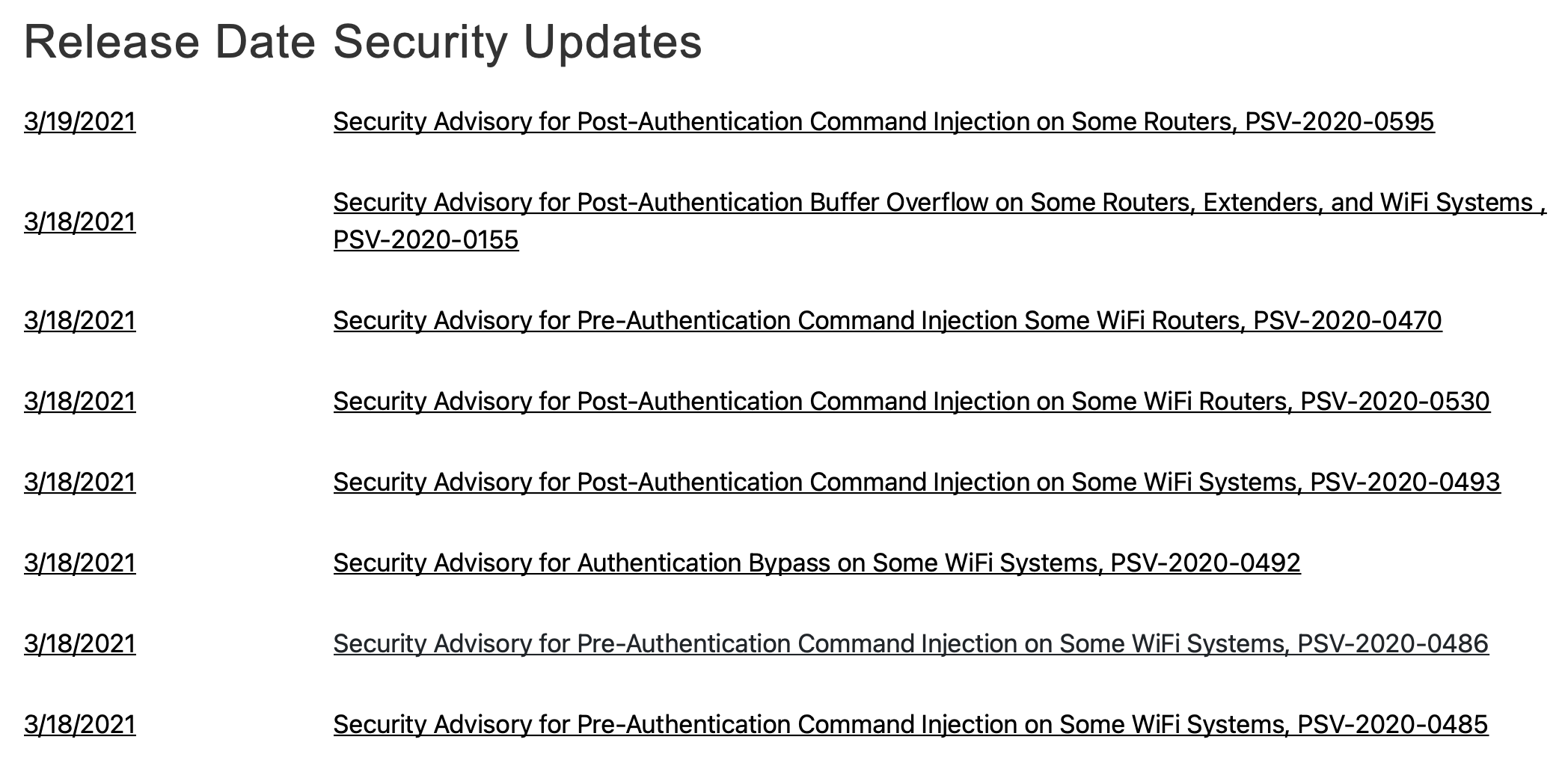
Product Security Updates
Consumer grade routers are an open invitation to be exploited. Just know that. I saw another article where some TP-Link routers have secret wifi networks which are bridged to your main wifi network. Beware the white panel van sitting in front of your house. 😃
Pick up any router box and it will tell you how blazingly FAST it is. Now look for the word SECURITY on the box. You probably won’t find it.
Anyway, just know this. If you hook your “bought at the store” router directly to your cable modem you are vulnerable.
A report done in June 2020 took 127 home routers and tested them. ALL of them had vulnerabilities. About 90% of them ran a Linux kernel however between 30-50% of them had some variant kernel version 2.6 which was last security patched about 2011. The devices that have newer kernel versions are probably the top of the line routers that cost hundreds of dollars aimed at the gamer market. Let me say this in plain English. If your router runs Linux kernel version 2.6 there is NO WAY to patch it.
“I don’t care” you say. “I’m boring”. “Nothing to see here”. Yep. All true in most peoples cases but imagine this. Lets say you are wide open and exploited and the bad guys put something on your hard drive and then link to it on the dark web. Something illegal like kiddie porn or whatever other terrible thing you can think of. Just think about trying to explain away to the guys in suits in the Black SUV why you are hosting kiddie porn.
Okay, that’s worst case for sure. And I DO run consumer grade routers. We all do. But there are a couple things you can do. One of course is to run them with Open Source firmware as I discussed, or you can put them behind a HARDWARE FIREWALL such as pfSense on Virtual LAN’s with Open Source Firmware and run an OS on your computer called Tails. Can North Korea, or the NSA still get you? Probably. But make them earn their pay.
Back to my situation. My R7800 has been dropping WiFi several times a day with OpenWRT so I decided to “upgrade” to DD-WRT. DD-WRT used to work on tons of hardware and it still does but it only actually works great on a few pieces of hardware these days. This is due to manufacturers using proprietary drivers, combining hardware devices and playing around flash memory layout. Makes it hard for the community to keep up.
THINK ABOUT WHAT I JUST SAID.
The manufacturers are making it hard for you to install Open Source firmware on their devices. Firmware that will provide you more security and possibly more SPEED AND STABILITY. Why would they do that? Maybe it is to save money in manufacturing, maybe it is to prevent hackers from dabbling around with their hardware and increasing their return rate and support calls……..I dunno. Or maybe it is that they don’t want you to have improved security. Your guess is as good as mine and it is probably a little bit of all three of those things.
The two or three darlings of the DD-WRT world right now are Netgear R7000, R7800, and R9000. Again, lots of other routers work but these are the best supported and most stable.
Another thing I like about the Netgear routers is that they provide you a method to easily rewrite firmware to the device when it turns into a brick by using a TFTP client. In my case I found that I COULD NOT migrate back to stock firmware on the R7800 with OpenWRT installed. It simply wouldn’t allow the firmware to write. So you follow the directions on that TFTP page and BAM you can flash back to Netgear factory firmware or even directly to DD-WRT. You can always recover from a bad flash or brick with these Netgear routers.
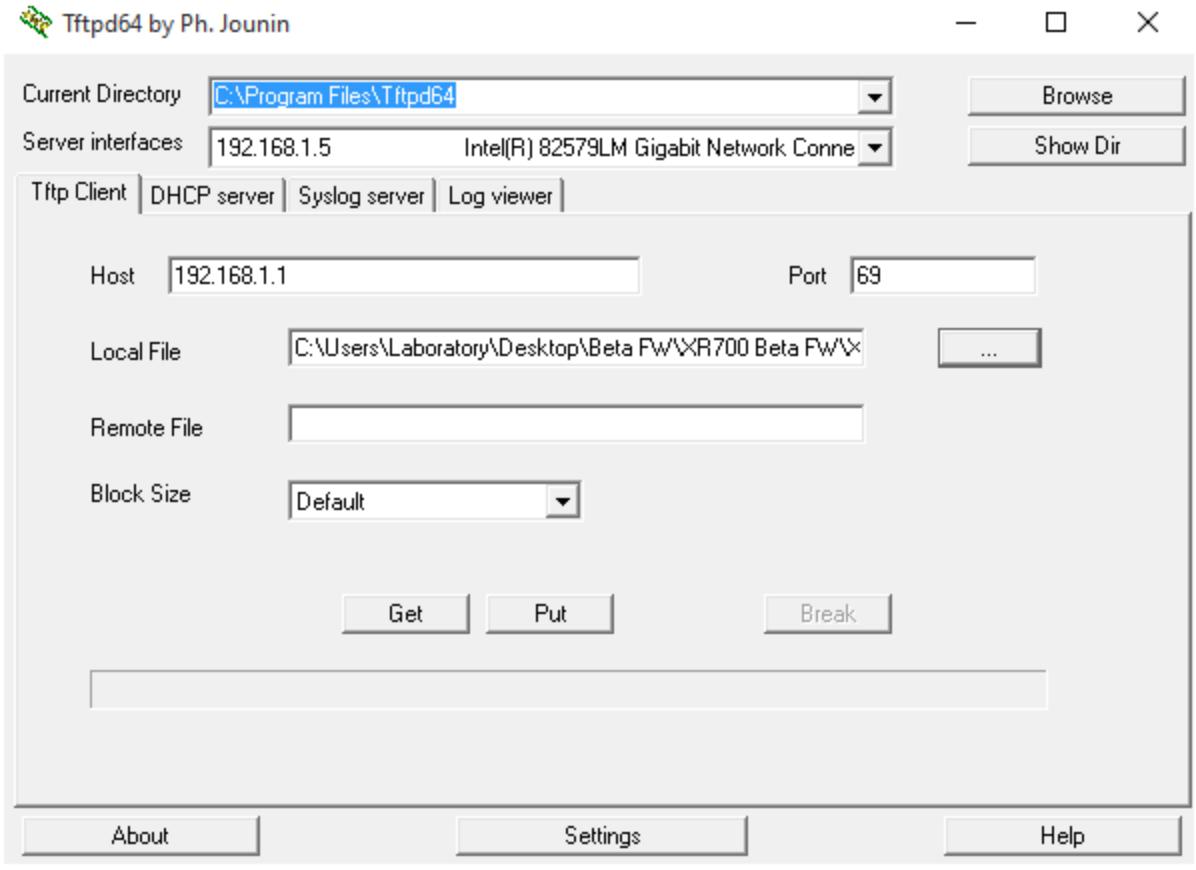
TFTP Client to recovery Netgear Router
It’s really as simple as hooking to the router via ethernet, and uploading firmware. Yeah, there are a few steps to follow but it is easy enough.
But make no mistake, I DO NOT RECOMMEND RUNNING NETGEAR ROUTERS WITH STOCK, OEM FIRMWARE. OPEN SOURCE, ALL THE WAY!
Anyway, I strongly recommend using Open Source Firmware and I recommend using it behind a hardware firewall as well. I won’t get into router settings to improve security but there are also a couple of tricks you can employ. One would be naming your Netgear dd-wrt wifi to the name of LinksysXXXX in the naming scheme that they do. Or naming your OpenWRT wifi network “dd-wrt”
The odds someone is going to exploit your Wifi, while not impossible, is fairly slim. They have to be reasonably close to you and know that it is your network. “John Hagensieker’s WIFI” might be a dead giveaway. “Bill Jones’s WiFI” might not be. See where I’m going with this?
I’ll leave you with one last story that I have told before on my blog. Nice lady across the street asks me to look at her cable router/modem and says her internet bill went up $100 one month and $200 the next month for extra bandwidth charges. She communicated to me that there was no way she was using that much data.
I logged into her router. She had a Smart TV, a laptop, and a phone connected to her network. There were a lot more than 3 devices connected to her router and I suspect it was some neighbor kids stealing her wifi. They either cracked the WPA password, guessed it, or maybe they figured out her IP address and simply used the default password to get into her router. Did you know that your router, which is connected DIRECTLY TO THE INTERNET probably has a password scheme like user: admin, password: password.
YOUR DEVICE, WHICH IS HOOKED DIRECTLY TO THE INTERNET, PROBABLY HAS A DEFAULT PASSWORD ASSIGNED TO IT………AND THAT PASSWORD IS WELL KNOWN AND PUBLISHED ON THE INTERNET BY THE MANUFACTURER.
I’m not kidding. admin:admin, root:admin admin: with no password. Simplicity for the manufacturer. Not for your security.
Good day, would you recommend a preflashed netgear router or purchase a stock model and install dd-wrt?
I understand that the install is technical and I have limited technical skills, although if you brick it the gear can be recovered