pfSense vs OPNsense
I don’t think most people give home network security much thought. Essentially you buy internet from a provider who gives you a modem of some sort. Then you attach a wifi router to it that you bought from Walmart or Target or even worse, one that the internet provider gives you. There is only one real way to have any semblance of home network security, and that is to have a hardware firewall. In this blog I’ll be discussing pfSense vs OPNsense. Both are free operating systems based on FreeBSD Unix. Don’t let that scare you though.
Anyway, your Walmart router sits on the shelf near the TV and never gets updated. Not that it would matter anyway because its security is roughly as porous as Swiss Cheese. If you don’t believe me take a few minutes to peruse routersecurity.org. If you dig around that site a bit you might even see my name there in a place or two!
Full Disclosure
Some years ago I discovered hardware firewalls and have not looked back since. Before i get started here I need to make some clarifying statements. Firewalls are not bulletproof. And the success of them depends a lot on them being configured correctly. Configuring both pfSense or OPNsense requires some level of geekiness and a bit of research to give yourself some modest amount of security. Even if you are a network security specialist, there are people out there or nation states capable of getting inside your network.
So What’s The Point?
The point is that most of those intrusion specialists could care beans about you. And the nation states really don’t care about you unless you’re up to something. But there is no shortage of people out there who who probe networks or ports looking for ways in. It’s my considered opinion that a lot of these intrusions are just designed to make your computer a bot to carry out massive denial of service attacks against other networks. Or people try to get into your networks………..because they can.
My Favorite Hacking Story
A few years ago a lady that lived across the street from me knew I was the neighborhood geek. She approached me one day and said her cable internet bill was several hundred dollars one month and several hundred the next. She told me she had a bandwidth capped plan that was massively exceeded but swore she never did much on any computer.
The first thing I asked her was “How many devices do you have connected to this router?” Her answer was a phone, a laptop, a single TV and a printer. When I logged into her router there were almost 2 dozen IP assignments and several people connected to WiFi. Of course WiFi means CLOSE. I surmised that the renters next door had hacked her WiFi which is surprisingly easy to do. And I suspect they were streaming content all day everyday. The first thing I did was to upgrade her router firmware and then kicked all the devices off and then changed all the passwords. POOF! No more high bills.
Anyway this woman realized AN ACTUAL FINANCIAL LOSS from being exploited.
What Else Can Happen?
Quick list:
- Your computer used as a bot to carry out an attack on another computer or network
- File snooping
- Attempt to gain banking or credit card information
- Placing keystroke loggers or rootkits on your devices
- Using your network to store illegal files or perform illegal transactions.
- UNWANTED RESOURCES THAT SLOW DOWN YOUR NETWORK CONSIDERABLY – this alone should be enough to implement some security
The first rule of hacking is to never hack from your own computer. Use someone else’s IP.
Hopefully I’ve convinced you that some security is in order. Here is a quick screenshot of attempted exploits towards my IP on the WAN interface over the last hour or two.
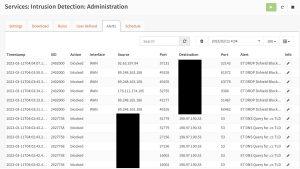
Intrusion Log
This is just WAN side. You should see the logs on the blocks on my LAN side. Ads, malware, etc. Let me say this:
IF YOU JUST HOOK THAT CHEAP ROUTER TO THAT ISP MODEM SOME OF THESE PROBES AND EXPLOIT ATTEMPTS COULD CONCEIVABLY BE SUCCESSFUL. THINK ABOUT THAT.
Building A Hardware Firewall Appliance
It’s pretty easy. You can use any old computer provided it has two network interface cards (NIC). The bad thing about old computers though is they are:
- Noisy with all the fans
- Consume a lot of watts of power
You want to buy an appliance specifically made for this. They can be had cheaply from places like Aliexpress or for a few more dollars of course from Amazon. Here is my current OPNsense project I just set up:
- Hardware Appliance
- 8GB of RAM – actually I put 16GB in but you really only need 8GB
- NVME SSD – I had a 256GB NVME drive laying around from a recent laptop upgrade I did. A 256GB new drive will set you back about $20 or so.

Firewall Appliance
So, yep. There is a financial investment involved in your security.
Which OS To Install?
Both pfSense and OPNsense are great firewall OS’s. Both are based on FreeBSD and OPNsense came from a fork of pfSense in around 2015. There are a lot of similarities and of course a lot of differences. As I mentioned I ran pfSense for several years until just a few days ago when I built my first OPNsense box.

So far I’m loving OPNsense. The layout is a little easier to find things and seems more logical.
With pfSense my intrusion detection and ad blocking came from two plugins. Snort and pfBlockerNG. Both can be free however I opted to purchase a Snort upgrade. Essentially, you get security rules that are a month old or so with the free edition.
So it is as well with OPNsense which uses its built in intrusion detection/prevention system called Suricata. Rule sets are free but are also 30 days old. The key difference here is that by agreeing to give up telemetry data to Proofpoint (keeper of Emerging Threats) you can have the pro version of Emerging Threats (ET) which are updated daily.
I did choose to do this.
You can’t go wrong with either pfSense or OPNsense. I think the consensus around the forums is that OPNsense is updated more, is a little easier to use, has a better layout, and has those free, up to date rulesets.
pfSense might be the stronger choice but is pretty geeky and may have a tougher learning curve.
VPN
I like to lock my network down to the outside world. When I am somewhere else and need to look at my security cams, or turn lights on and off with my home automation I simply VPN back into my network. For years I have run OpenVPN on pfSense. And it has worked for me with a fair amount of simplicity.
WireGuard
Since I’m running a new OS instance of OPNsense I decided to run a new VPN as well. WireGuard purports to be leaner, meaner, faster, and uses state of the art cryptography. It works by sharing public keys between client and server. This is pretty similar to encryption setup on emails. While it took me a couple tries to get it working with my laptop it wasn’t too difficult to set up.
I had to do a little head scratching to set up a 2nd device (my iPhone) as none of the tutorials I found covered that very well. But after a few tries I had an AH HA moment and figured out what I was doing wrong. Is WireGuard better than OpenVPN as a VPN? I dunno but my WireGuard instance is working like a champ and it seems more secure with the cryptography to me.
Summation
I know I didn’t get into any detail or tech setup wizardry and I didn’t dive too deep. The point I hoped to make with this blog is that YOUR NETWORK AS IT IS, IS NOT SECURE, not even a little bit, and the only way to have a modicum of security is to add a hardware firewall device. Either OS, pfSense and OPNsense can be configured to be a very secure hardware firewall but there is a learning curve that a lot of people just won’t take the time to overcome. And there is a hardware cost as well.
But a hardware firewall is essentially the only way.
It would be nice if you could buy a pre-configured device and just drop it in place but you can’t. Hardware firewalls can be too restrictive. You may want to filter out certain things, and I might now want to. You might have kids that need to be shut down from gaming, chat, or porn. Many folks might be empty nesters. You can filter anything with a firewall to include politics. Just as your work shuts you down from watching YouTube…….so it can be on your hardware firewall.
I simply cannot set up the parameters of your network without having a very extensive interview. Nor could you set up mine.
When I was running pfSense my firewall was so restrictive it would sometimes lock everything down. I’ve learned to ease up a bit and have deployed my protection as such with this new firewall while still trying to filter the crap and junk out.
John, Great to see you back!!
Hey John, great blog. I am researching ways to get coreboot on those cheap hardware firewalls and found your article from 2020 when you managed to do just that.
Back then you said “an Open Source OS really needs to sit on top of an Open Source firmware for maximum security.” Is this no longer a concern for you?
Unrelated, since I saw some posts about watches: Have you heard about the Sensor Watch project? https://www.sensorwatch.net/
Might be right up your alley…
Thanks for the nice comments. Ideally, I’d like Coreboot on all my appliances but sometimes I impulse buy or catch a good deal. That SensorWatch looks like something right up my alley. Thanks!
I know I’m commenting on an old post, but would love to hear about your “ah ha” moment, what was the issue, and how it was resolved. Thanks!